LDAP Account Manager Pro is an extended version of LAM which focuses on enterprise usage. It helps you to lower your administration costs by providing enhanced tools for your users and deskside support staff.
Features
See our feature matrix for details. All LAM Pro features are documented in the LAM manual.
User self service
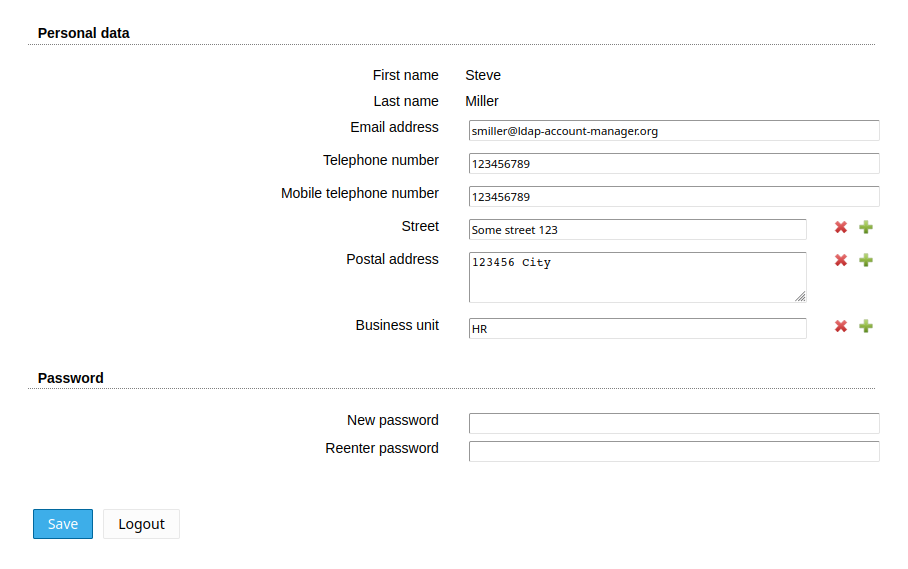
This special feature allows your users to change certain LDAP data (e.g. telephone number or password) themselves.
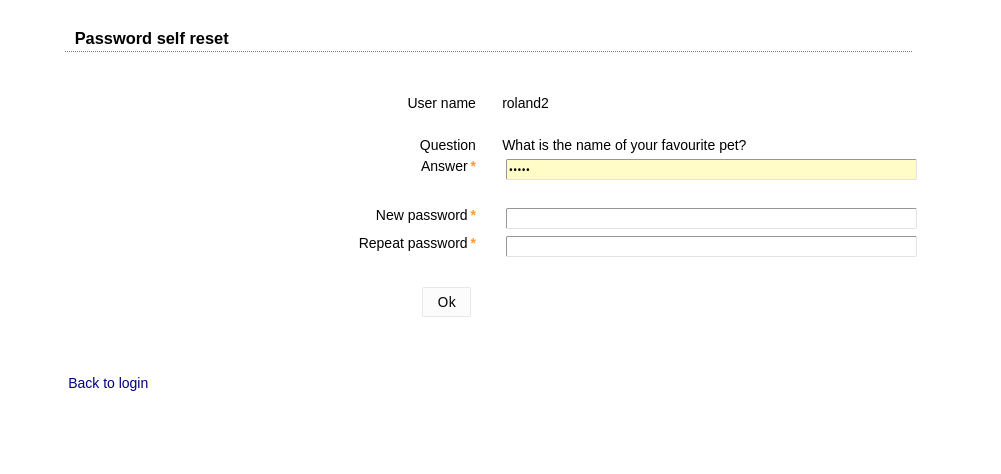
LAM Pro can show a "Forgot password?" link that allows your users to reset their passwords by answering a security question. You can allow users to create their own accounts (incl. approval by admin). The "Request access" module allows users to request group memberships (group of (unique) names). The requests are approved by the group owners and optionally by a separate approver group.

Top features:
- Password self reset with security question and/or email verification
- User self registration
- Allows to integrate external CSS files to match your corporate design
- Support for custom attributes
Screenshots:
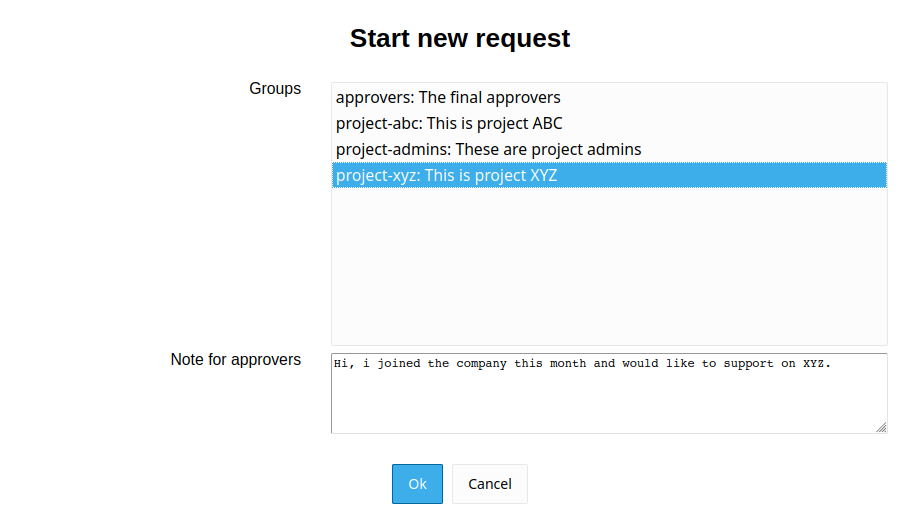
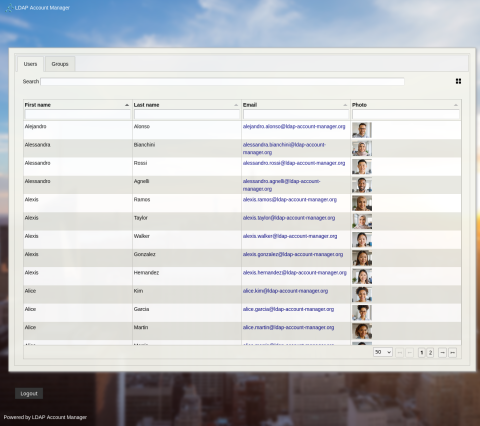
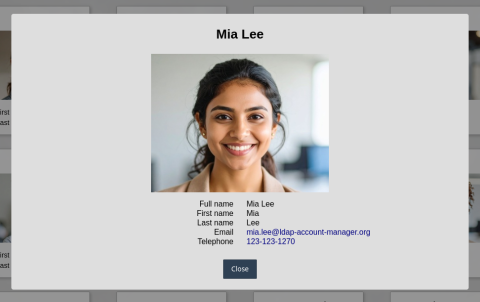
White pages
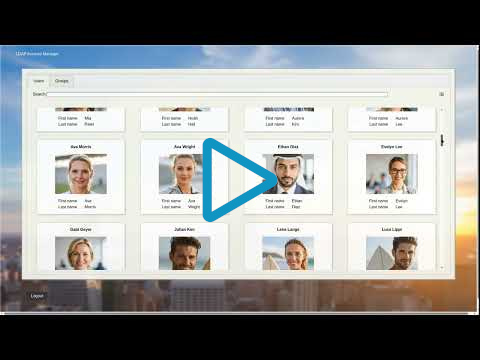
LAM Pro white pages allows to create read-only views to search for e.g. user contact information or any other LDAP data (groups, rooms, hardware entries, ...). The views can be accessed anonymously or authenticated.
This is a great tool to create a simple user directory to lookup colleagues.
|
|

|
|
See it action:
Additional account modules
LAM Pro provides additional account modules to support more LDAP object classes.

You can even manage your own attributes and object classes with our custom fields module. The input fields can be defined using a simple GUI that provides a large range of types like text, number, date, LDAP lookup, ...
LAM Pro modules:
- AD LDS: users and groups
- Alias: can be used to define aliases for user accounts.
- Apache Guacamole: Guacamole configuration
- Auto delete: uses dynamic directory services (DDS) to delete entries by LDAP server.
- Custom fields: manage your own custom LDAP object classes
- Device: manages serial numbers and other information for host entries.
- DNS entries: PowerDNS and bind DLZ/dyndb entries
- Group of (unique) names, group of members: these modules can be used to represent group relations. Since they allow DNs as members you can also use them to represent nested groups.
- Heimdal/MIT: manage your Heimdal/MIT Kerberos accounts
- IP host: IP addresses for host accounts
- Named object: rfc2307bis groups
- NIS object, automount: used to define network mounts.
- Oracle databases: replacement for tnsnames.ora
- Organizational roles: organizationalRole object class
- PPolicy: password policy overlay for OpenLDAP
- QMail: qmail user support
- RFC2307bis schema: some distributions (e.g. Suse) use this schema for group accounts.
- Simple Security Object: entries with password only
- Sudo role: sudo role management that replaces /etc/sudoers
- Kopano: management of Kopano users, groups and servers
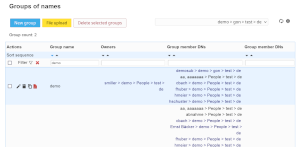
Screenshots:
 |
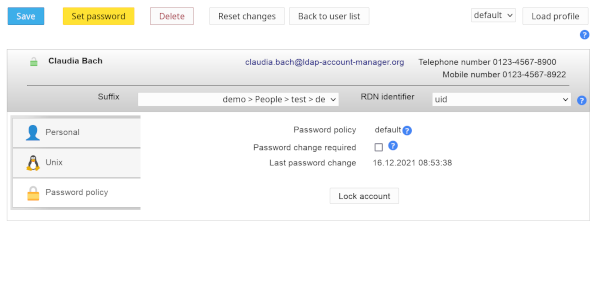 |
| Group of names | PPolicy |
Custom scripts

LAM Pro allows you to run any script on your server when an account is created/modified/deleted. You can specify if a script should be run before or after the LDAP modification. You can also specify LDAP attributes as parameters for the script calls. This allows you to further automate your management processes.
The LAM Pro self service also supports custom scripts.
Cron jobs

Cron jobs can be used to e.g. notify users that their passwords will expire soon. LAM checks e.g. the PPolicy password policy and sends a password reminder email before your user's passwords expire.
There is a number of jobs available to notify users and delete/move accounts. LAM Pro supports Windows, Shadow, PPolicy, 389ds, FreeRadius and QMail.
Access levels
You can define if LAM should allow write access, password changes or only read access.
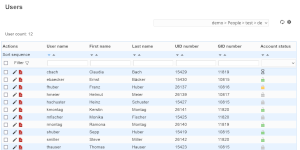
Screenshots of read-only mode:
 |
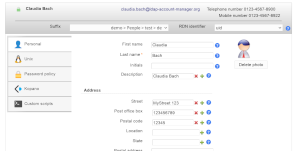 |
| No controls to add/remove accounts | No save button on account pages |
Password reset page
This special page allows your deskside support staff to reset the passwords of your users. LAM can generate random passwords and you can send the passwords directly by mail.
If you set the access level of your server profile to "Change passwords" then LAM will not allow any changes to the LDAP database except password changes via this page. The account pages will be still available in read-only mode.
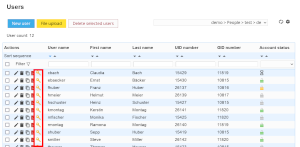
Screenshots:
 |
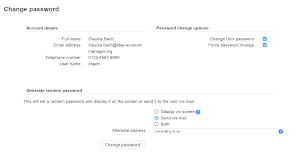 |
| Access from account list | Password reset page |
Order LAM Pro
Please visit our online shop to order a LAM Pro license.
LAM Pro customers