On top of the page you see the link to the user login page. Copy this link address and give it to your users.
Below the link you can specify several options.

Table 7.1. General options
| Server address | The address of your LDAP server. For LDAP+SSL use "ldaps://myserver" |
| Activate TLS | Activates TLS encryption. Please note that this cannot be combined with LDAP+SSL ("ldaps://"). |
| LDAP suffix | The part of the LDAP tree where LAM should search for users |
| LDAP search attribute | Here you can specify if your users can login with user name + password, email + password or other attributes. |
| Follow referrals | By default LAM will not follow LDAP referrals. This is ok for most installations. If you use LDAP referrals please activate the referral option in advanced settings. |
| LDAP user + password | The DN and password which is used to search for users in the LDAP database. It is sufficient if this DN has only read rights. If you leave these fields empty LAM will try to connect anonymously. |
| Use for all operations | By default LAM will use the credentials of the user that logged in to self service for read/modify operations. If you select this box then the connection user specified before will be used instead. Please note that this can be a security risk because the user requires write access to all users. You need to make sure that your LAM server is well protected. |
| Additional LDAP filter | Use this to enter an additional LDAP filter (e.g. "(objectClass=passwordSelfReset)") to reduce the number of accounts who may use self service. |
| Authentication method | The default method is user and password login. You can also enable HTTP authentication for your users. This way the web server is responsible to authenticate your users. LAM will use the given user name + password for the LDAP login. To setup HTTP authentication in Apache please see this link. If you use Okta or OpenID for 2FA then you can also select to trust the 2FA provider. In this case the user does not need to enter any password in LAM itself (SSO). |
| Default language | This language is preselected on login. |
| Enforce language | Disables language selection and uses default language. |
| Time zone | Please provide your time zone. |
| Base URL | Please enter the base URL of your webserver (e.g. https://www.example.com). This is used to generate links in emails for password self reset and user self registration. |
| Login attribute label | This is the description for the LDAP search attribute. Set it to something which your users are familiar with. |
| Password field label | This text is placed as label for the password field on the login page. LAM will use "Password" if you do not enter any text. |
| Login caption | This text is displayed on the login page inside the login mask. |
| Login footer | This text is displayed on the login page below the login mask. |
| Main page caption | This text is displayed on the self service main page where your users change their data. |
| Main page footer | This text is displayed as footer on the self service main page where your users change their data. |
| Page header | This HTML code will be placed on top of all self service pages. E.g. you can use this to place your custom logo. Any HTML code is permitted. |
| Base color | Here you can change the background color for the user pages. |
| Additional CSS links | Here you can specify additional CSS links to change the layout of the self service pages. This is useful to adapt them to your corporate design. Please enter one link per line. |
LAM supports 2-factor authentication for your users. This means the user will not only authenticate by user+password but also with e.g. a token generated by a mobile device. This adds more security because the token is generated on a physically separated device (typically mobile phone).

Configuration
Please see the 2FA appendix for configuration details of the different providers.
Remember device
You can allow users to remember the 2FA device for privacyIDEA, WebAuthn and YubiKey. When a device is remembered then users can login for the specified time without presenting their 2nd factor.
The password for the device remembering is used to authenticate the device data. It can be any long passphrase (use > 30 characters). LAM auto-generates one for you. If you change the passphrase then all device data gets invalid and users need to represent their 2nd factor again (which then can be saved again).

Login
After logging in with user + password LAM will ask for the 2nd factor. If the user has setup multiple factors then he can choose one of them.

LAM Pro can optionally display a captcha to verify that logins are not from robots. Captchas will be displayed when you tick the checkbox to secure login with a captcha. The supported captcha providers are:
Google reCAPTCHA
You will need the site and secret key for your domain. They can be retrieved from here: https://www.google.com/recaptcha
Please note that your web server must be able to access "https://www.google.com/recaptcha/api/siteverify" to verify the captchas.
Friendly Captcha
Please enter your site (see applications) and API key. The web server must be able to contact "https://api.friendlycaptcha.com" for verification.
hCaptcha
Please enter your site and secret key (not API key). The web server must be able to contact "https://hcaptcha.com" for verification.

This section is only required if you want to display file system quotas or create home directories via lamdaemon.
Server list format options:
"server": "server" is the DNS name of your script server
"server:NAME": NAME is the display name of this server
"server:NAME:/prefix": /prefix is the directory prefix for all operations. E.g. creating a home directory "/home/user" would create "/prefix/home/user" then.
You need to provide a fixed user name.
Self service requires a SSH connection with SSH key. Please generate a SSH key pair and provide the location to the private key file. If the key is protected by a password you can also specify it here.
In case you want to create home directories during user self registration please provide the rights for it (e.g. 750).

Here you can specify what input fields your users can see. It is also possible to group several input fields.
Please use the arrow signs to change the order of the fields/groups.
You may also set some fields as read-only for your users. This can be done by clicking on the lock symbol. Read-only fields can be used to show your users additional data on the self service page that must not be changed by themselves (e.g. first/last name).
Sometimes, you may want to set a custom label for an input field. Click on the edit icon to set your own label text (Personal: Department is relabeled as "Business unit" here).

This is a list of input fields you may add to the self service page.
Table 7.2. Self service fields
| Account type | Option | Description |
 Account locking Account locking | Password expiration | Read only value of password expiration date |
 Asterisk (voicemail) Asterisk (voicemail) | Sync Asterisk password with Unix password | This is a hidden field. It will update the Asterisk password each time the Unix password is changed. |
 Group of names Group of names | Group memberships (read-only) | |
 Kerberos Kerberos | Sync Kerberos password with Unix password | This is a hidden field. It will update the Kerberos password each time the Unix password is changed. |
 Kolab Kolab | Delegates | Allows to manage delegate permissions |
| Invitation policy | Invitation policy management | |
 Password policy Password policy | Last password change | read-only |
 Password self reset Password self reset | Question | Security question selection |
| Answer | Security answer | |
| Backup email | (External) backup email address that has no relation to user password. | |
 Personal Personal | Business category | |
| Car license | ||
| Department | ||
| Description | ||
| Email address | ||
| Fax number | ||
| First name | ||
| Home telephone number | ||
| Initials | ||
| Job title | ||
| Last name | ||
| Location | ||
| Mobile number | ||
| Office name | ||
| Organisation | ||
| Organisational unit | ||
| Photo | Shows the user photo if set. The user may also remove the photo or upload a new one. | |
| Postal address | ||
| Postal code | ||
| Post office box | ||
| Registered address | ||
| Room number | ||
| State | ||
| Street | ||
| Telephone number | ||
| User certificates | Upload of user certificates in PEM or DER format | |
| User name | ||
| Web site | ||
 Mail routing Mail routing | Local address (read-only) | |
| Mail routing address (read-only) | ||
 OpenLDAP TOTP OpenLDAP TOTP | OpenLDAP TOTP token + serial number | See OpenLDAP TOTP |
 Quota Quota | Quota (read-only) | Displays the user's system quote. Requires lamdaemon configuration. |
 Samba 3 Samba 3 | Password | Input field to set a new NT/LM password. The attribute "sambaPwdLastSet" is updated if it existed before. |
| Sync Samba LM password with Unix password | This is a hidden field. It will update the Samba LM password each time the Unix password is changed. | |
| Sync Samba NT password with Unix password | This is a hidden field. It will update the Samba NT password each time the Unix password is changed. | |
| Update attribute "sambaPwdLastSet" on password change | Updates the password timestamp when password is synchronized with Unix. | |
| Last password change (read-only) | Displays the date and time of the user's last password change. | |
 Shadow Shadow | Account expiration date (read-only) | |
| Last password change (read-only) | Displays the date and time of the user's last password change (Unix). | |
 Windows (AD, AD LDS, Samba 4) Windows (AD, AD LDS, Samba 4) | Password | Change the user's password |
| Location | ||
| Mail alias (read-only) | ||
| Office name | ||
| Postal code | ||
| Post office box | ||
| Proxy-Addresses (read-only) | ||
| State | ||
| Street | ||
| Telephone number | ||
| Web site | ||
 Unix Unix | Common name | |
| Group memberships (read-only) | ||
| Login shell | ||
| Password | This is also the source for several password synchronization options. | |
| Sync Unix password with Windows password | This is a hidden field. It will update the Unix password each time the Windows password is changed. | |
 WebAuthn WebAuthn | WebAuthn devices | Allows the user to manage his webauthn/FIDO2 security keys. |
 Kopano Kopano | "Send as" privileges | Define user who may send mails as this user |
| Email aliases | Email aliases | |
 PyKota PyKota | Balance (read-only) | Current balance for printing |
| Total paid (read-only) | Total money paid | |
| Payment history | History of user payments | |
| Job history | History of printed jobs |
This allows to configure some module specific options (e.g. custom scripts or password hash type).

LAM Pro can check the password history and minimum age for Samba 3 password changes. In this case please provide the LDAP suffix where your Samba 3 domain(s) are stored.
If you leave the field empty then no history and age checks will be done.
Password history: depending on your LDAP server you might need ascending or descending order. Just switch the setting if the password history is not correctly updated.

Schema installation
Please install the LDAP schema as described here.
Settings
You can allow your users to reset their passwords themselves. This will reduce your administrative costs for cases where users forget their passwords.
To enable this feature please activate the checkbox "Enable password self reset link".
Hint: Please note that LAM Pro uses security questions by default. Activate confirmation mails and then deactivate security questions if you want to use only email validation.
The password reset must be finished by the user within 24h or the process must be restarted.

Identification method, used LDAP attributes:
Email: mail
Employee number: employeeNumber
Self service login attribute: same as configured on first tab of self service profile
User name: uid
User name and email address: uid and mail
User name or email address: uid and mail
You can now configure the minimum answer length for password reset answers. This is checked when you allow you users to specify their answers via the self service. Additionally, you can specify the text of the password reset link (default: "Forgot password?"). The link is displayed below the password field on the self service login page.
Next, please enter the DN and password of an LDAP entry that is allowed to reset the passwords. This entry needs write access to the attributes shadowLastChange, pwdAccountLockedTime and userPassword. It also needs read access to uid, mail, passwordSelfResetQuestion and passwordSelfResetAnswer. Please note that LAM Pro saves the password on your server file system. Therefore, it is required to protect your server against unauthorised access.
Please also specify the list of password reset questions that the user can choose.
Please note that self service and LAM admin interface are separated functionalities. You need to specify the list of possible security questions in both self service profile(s) and server profile(s).
You can inform your users via mail about their password change. The mail can include the new password by using the special wildcard "@@newPassword@@". Additionally, you may want to insert other wildcards that are replaced by the corresponding LDAP attributes. E.g. "@@uid@@" will be replaced by the user name. See here for setting up your SMTP server.
LAM Pro can send your users an SMS/email with a confirmation link to validate their SMS/email address. If you select to send an SMS then the email mechanism will only be used if no mobile phone number was found for this user. You also need to setup the SMS settings.
Confirmation mails should only be used if the email account is independent from the user password (e.g. at external provider) or you use the backup email address feature. The mail body must include the confirmation link by using the special wildcard "@@resetLink@@". Additionally, you may want to insert other wildcards that are replaced by the corresponding LDAP attributes. E.g. "@@uid@@" will be replaced by the user name.
There is also an option to skip the security question at all if email verification is enabled. In this case the password can be reset directly after clicking on the confirmation link. Please handle with care since anybody with access to the user's SMS/mail account can reset the password.
Captcha support
LAM Pro can optionally display a captcha to verify that password resets are not from robots. The captcha provider is configured on "General settings" tab.
Captchas will be displayed when you tick the checkbox to use a captcha.

Troubleshooting:
1. You get messages like "Unable to find user account."
This can have multiple reasons:
security questions enabled but no security question and/or answer set for this user
user name + email combination does not exist
no connection to LDAP server
Turn on logging in LAM's main configuration settings. The exact reason is logged on notice level.
2. You do not see security question and answer fields when logged into self service.
Probably, the user does not have the object class "passwordSelfReset" set. You can do this in admin interface. If you have multiple users to change then use the Multi Edit Tool to add the object class.
New fields for self service page
There are special fields that you may put on the self service page for your users. These fields allow them to change the reset questions and its answers. It is also possible to set a backup email address to reset passwords with an external email address.

This is an example how can be presented to your users on the self service page:

Password reset link
After activating the password self reset feature there will be a new link on the self service login page. The text can be configured as described above (default: "Forgot password?").

When a user clicks on the link then he will be asked for identification with his user name and email address.

LAM Pro will use this information to find the correct LDAP entry of this user. It then displays the user's security questions and input fields for his new password. If the answer is correct then the new password will be set. Additionally, pwdAccountLockedTime will be removed and shadowLastChange updated to the current time if existing.

Prefilling the input fields
You might want to provide personalized URLs to your users that already prefill the fields in first step of password self reset. This can be done by adding an additional URL parameter with the attribute name in lower case.
LAM will not generate these URLs for you. This needs to be done by the system that provides the URL to your user.
Examples:
/lam/templates/selfService/selfServiceSP.php?scope=user&name=myProfile&page=passwordSelfReset&language=en_GB.utf8&uid=yourUserId
/lam/templates/selfService/selfServiceSP.php?scope=user&name=myProfile&page=passwordSelfReset&language=en_GB.utf8&mail=yourUserId@company.com
/lam/templates/selfService/selfServiceSP.php?scope=user&name=myProfile&page=passwordSelfReset&language=en_GB.utf8&uidmail=yourUserId (for "user or email" method)
/lam/templates/selfService/selfServiceSP.php?scope=user&name=myProfile&page=passwordSelfReset&language=en_GB.utf8&customattribute=yourUserId
With LAM Pro your users can create their own accounts if you like. LAM Pro will display an additional link on the self service login page that allows you users to create a new account including email validation (see here for setting up your SMTP server).
You enable this feature in your self service profile. Just activate the checkbox "Enable self registration link".

Options:
Link text: This is the label for the link to the self registration. If empty "Register new account" will be used.
Admin DN and password: Please enter the LDAP DN and its password that should be used to create new users. This DN also needs to be able to do LDAP searches by uid in the self service part of your LDAP tree.
Object classes: This is a list of object classes that are used to build the new user accounts. Please enter one object class in each line. If you use LAM Pro password self reset feature then do not forget to add "passwordSelfReset" here.
Attributes: This is a list of additional attributes that the user can enter. Please note that user name, password and email address (attribute "mail") are mandatory anyway and need not be specified. Just in case you use the legacy attribute "email" for account it needs to be specified (attribute "mail" will then not be shown).
Each line represents one LDAP attribute. The settings are separated by "::". The first setting specifies the field type. The second setting is the LDAP attribute name (add ";binary" to attribute names for file upload). Depending on the field type you can enter additional options:
Table 7.3.
| Description | Type | Attribute name | First option | Second option | Third option |
| An optional input field that is displayed on the registration page. | optional | e.g. "givenName" or "jpegPhoto;binary" | Label that is displayed on page | Optional regular expression for validation (e.g. "/^[0-9a-zA-Z]+$/"). For binary fields the file name will be checked. | Validation message if value does not match validation expression. |
| A required input field that is displayed on the registration page. Self registration cannot be done if such a field is left empty by the user. | required | e.g. "sn" or "jpegPhoto;binary" | Label that is displayed on page | Optional regular expression for validation (e.g. "/^[0-9a-zA-Z]+$/"). For binary fields the file name will be checked. | Validation message if value does not match validation expression. |
| Constant attribute value, not visible for the user. Can be used to set some initial values or data that must not be edited by the user. | constant | e.g. "homeDirectory" | attribute value, supports wirldcards to insert other attribute values (e.g. "@@uid@@") | ||
| Auto-numbering for attributes such as uidNumber. Will do a search for attribute values in the given range and use highest value + 1. | autorange | e.g. uidNumber | LDAP search base, e.g. ou=people,dc=company,dc=com | Minimum value, e.g. 1000 | Maximum value, e.g. 2000 |
For a syntax description of validation expressions see here. Validation is optional, you can leave these options blank.
Examples:
Unix account:
optional::givenName::First name::/^[[:alnum:] ]+$/u::Please enter a valid first name.
required::sn::Last name::/^[[:alnum:] ]+$/u::Please enter a valid last name.
constant::homeDirectory::/home/@@uid@@
autorange::uidNumber::ou=people,dc=company,dc=com::10000::20000
If you use the object class "inetOrgPerson" and do not provide the "cn" attribute then LAM will set it to the user name value.
Active Directory/Samba4:
required::cn::Common Name::/^[[:alnum:] ]+$/u::Enter common name.
constant::userPrincipalName::@@uid@@@samba4.test
constant::sAMAccountName::@@uid@@
constant::userAccountControl::512
Binary file:
required::jpegPhoto;binary::Photo::/.jp(e)?g$/i::Please select a JPG file
Please note that only simple input boxes are supported for account registration. The user may log in to self service when his account was created to manage all his attributes.
Create home directory: This will create the home directory via lamdaemon. The user must have the following attributes: uid, uidNumber, gidNumber, homeDirectory
Approval
You can send the account request to an administrator for approval. The email will include links for approval/reject. Please use the wildcards @@approveLink@@ and @@rejectLink@@ for this.
If the request was rejected then no email will be sent to the user.

Captcha support
LAM Pro can optionally display a captcha to verify that registrations are not from robots. The captcha provider is configured on "General settings" tab.
Captchas will be displayed when you tick the checkbox to use a captcha.

User view:
The user can register by clicking on a link on the self service login page:

Here he can insert the data that you specified in the self service profile:

LAM will then send him an email with a validation link that is valid for 24 hours. When he clicks on this link then the account will be created in the self service user suffix. The DN will look like this: uid=<user name>,...
Use this feature to allow your users to request access for group memberships/ownerships. Requests will require the approval by the group owners/managers and optionally a special approver group (leave empty for owner/manager approval only).
Setup cleanup
Please use the global cron job to clean any outdated requests or history entries. Here you can configure how long requests should be kept open and when to clean the history.
Module Configuration
First, the request access module needs to be activated and configured on tab "Module settings". Here tick "Enable request access" and provide the information where your groups are located.
Group of names, group of unique names and Windows groups are supported. The LDAP filter is optional, LAM will offer the user only groups of (unique) names or Windows groups that have defined owners/managers unless an additional owner group is defined.


The email body texts support wildcards. You can use group owner/approver LDAP attributes in the form @@attribute@@ (e.g. @@uid@@ for the user name).
The requester's LDAP attributes can be used in the form $$attribute$$ (e.g. $$uid$$ for the user name). This is supported for mails to the group owners/managers and the approval/deny mails to the requester.
The wildcard $$requested_groups$$ will resolve to the requested groups. This is available for all mails.
In addition, $$requested_groups_member$$ and $$requested_groups_owner$$ can be used to inject the groups for member or owner requests (only emails for approved/denied requests).
Use the wildcard $$requested_type$$ in owner emails to get the request type (Member/Owner). The request type label is replaced in the language of the requester's self service session.
The wildcard $$requester_notes$$ resolves to the requester's optional notes. This is available for the mails to the group owners/managers.
Use $$request_comment$$ to inject the owner's or approver's comment. This can be used in mails to approvers and requesters.
The wildcards $$approveLink$$ and $$rejectLink$$ resolve to an URL that allows to approve/deny all requests listed in $$requested_groups$$. This is available for the mails to the group owners/managers and approvers. Use it as target URL for a link inside the email body.
The wildcard $$membershipRevocationTime$$ resolves to the revocation date of the membership if set. It is available for the mails to the approvers.
Example for owner email:
Dear @@cn@@,
a new access request was created by $$cn$$:
Requested groups: $$requested_groups$$
Reason: $$requester_notes$$
Approve all: $$approveLink$$
Deny all: $$rejectLink$$
Please check here (link to self service) for details.
Best regards,
IT team
Example for approver email:
Dear @@cn@@,
there are new access requests waiting for approval:
$$requested_groups$$
Comment: $$request_comment$$
Approve all: $$approveLink$$
Deny all: $$rejectLink$$
Please check here (link to self service) for details.
Best regards,
IT team
Example for approved/denied request email:
Dear $$cn$$,
your access request was approved/denied.
Requested groups: $$requested_groups$$
Comment: $$request_comment$$
Best regards,
IT team
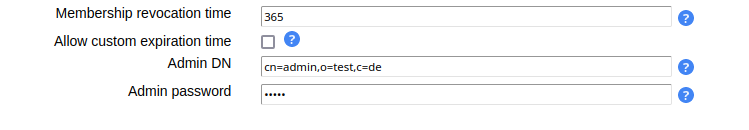
Membership Revocation
You can select to revoke memberships after a given time. LAM will then remove them using global cron job once the time is reached. Please configure the following settings. If you use multiple self-service profiles for requester/owner/approver views then you need to configure this in the one that group owners use.
If you do not specify a revocation time then memberships/ownerships will not expire unless a custom revocation time is used. Allowing custom revocation times enables group owners to enter a custom date of revocation or no revocation time. The admin DN and password are used to perform the LDAP operation to remove the memberships.
Field Configuration
Next, the fields need to be added to the "Page layout" tab. There are three fields:
Request Access: Request access - User view that allows to initiate the process.
Request Access: Owner view - Owner view for group owners.
Request Access: Approver view - Approver view for approver group
Request Access: History of own requests - History of the current user's requests
Request Access: History of requests - History of all requests
Users that have no approver role see only requests for their managed groups
Users that are neither approver nor managing groups will not see anything
Request access: Revocation information - Displays when roles will be revoked by the system
Users that have no approver role see only their managed groups
Users that are neither approver nor managing groups will not see anything
You can set custom labels using the pencil icon.

Request view
The user sees a button to open the new request dialog. Here the groups can be selected and an optional note can be provided.


Owner/approver view
Once the request is created, all owners of the respective groups get an email notification. They can then enter self service and view their open requests.
If an approver group is configured then its members will get an email notification after owner approval. In case no approver group is configured, the permissions are directly granted when the owner approves the request.

Own request history
Request history
This module allows you to manage LDAP attributes that are not covered by the other LAM modules (e.g. if you use custom LDAP schemas). You can fully define how your input fields look like:
Label
LDAP attribute name
Unique name for field
Help text
Read-only display
Field type: text, password, text area, checkbox, radio buttons, select list, file upload, LDAP date (and time), constant
Validation via regular expression
Error message if validation fails
To create custom fields for the Self Service please edit your Self Service profile and switch to tab "Module settings". Here you can add a new field. Simply fill the fields and press on "Add".
Please note that the field name cannot be changed later. It is the unique ID for this field.
After you created your fields please press on "Sync fields with page layout". Now you can switch to tab "Page layout" and add your new fields like any other standard field.

Examples for fields and their representation in Self Service:
Text field:
Text fields allow to specify a validation expression and error message.
You can also enable auto-completion. In this case LAM will search all accounts for the given attribute and provide auto-completion hints when the user edits this field. This should only be used if there is a limited number of different values for this attribute.
In case your field is a date value you can show a calendar for easy editing.
Example calendar formats:
d.m.Y: 31.12.2025
Y-m-d: 2025-12-31
d M, y: 31 Dec, 25
d MM, Y: 31 December, 2025
You can escape wildcards with "\". E.g. "d.m.Y \d" will result in "31.12.2025 d".

Presentation in Self Service:

Password field:
You can also manage custom password fields. LAM Pro will display two fields where the user must enter the same password. You can hash the password if needed.

Presentation in Self Service:

Text area:
This adds a multi-line field. The options are similar to text fields. Additionally, you can set the size with the number of columns and rows.
Please note that the validation expression should be set to multi-line. This is done by adding "m" at the end.

Presentation in Self Service:

Checkbox:
Sometimes you may want to allow only yes/no values for your LDAP attributes. This can be represented by a checkbox. You can specify the values for checked and unchecked. The default value is set if the LDAP attribute has no value.

Presentation in Self Service:

Radio buttons:
This displays a list of radio buttons where the user can select one value.
You can specify a mapping of LDAP attribute values and their display (label) on the Self Service page. To add more mapping fields please press "Add more mapping fields".

Presentation in Self Service:

Select list:
Select lists allow the user to select a value in a large list of options. The definition of the possible values and their display is similar to radio buttons.
You can also allow multiple values.

Presentation in Self Service:


LDAP search select list
This is similar to "Select list" but the option are read from LDAP. You can use this to define e.g. a DN selection list. Multiple values are supported.

LDAP suffix: The LDAP DN that is used as starting point to search for LDAP entries.
LDAP filter: Only LDAP entries that match this filter will be used. If all entries should be used then use "(objectclass=*)".
Attribute name: The values of this attribute will be used to build the selection list.
Display attributes: List of attributes to show as label for the options in select box. Attribute wildcards are surrounded by "$", e.g. "$cn$" will be replaced by "cn" attribute. Default is "$dn$".
Presentation:

LDAP date
Use this for LDAP attributes with syntax "Generalized Time" (1.3.6.1.4.1.1466.115.121.1.24).
LAM will automatically set hour/minute/second to "0". If this is not intended please use type "LDAP date and time".

Presentation:
LAM will display a calendar to select the date.

LDAP date and time
Use this for LDAP attributes with syntax "Generalized Time" (1.3.6.1.4.1.1466.115.121.1.24).
LAM can convert the displayed value to the configured time zone of your server/self service profile. In this case, please activate "Display in local time".

Presentation:
LAM will display a calendar to select the date and time.

Constant value
This will set the attribute to a constant value. You can also specify wildcards to inject other attribute's values.

Wildcards:
%attribute%: attribute value
@attribute@: first character of attribute
?attribute?: first character of attribute in lower case
!attribute!: first character of attribute in upper case
??attribute??: attribute in lower case
!!attribute!!: attribute in upper case
((attribute)): space if attribute is set
§attribute|;§; attribute values separated by ";" (you can set other separators if you want)
Examples for attributes gn="Steve", sn="Miller" and memberUid=("user1", "user2") (specified value -> resulting LDAP value):
Table 7.4.
| Constant value | Resulting LDAP value |
|---|---|
| my constant | my constant |
| %gn% | Steve |
| %gn%((gn))%sn% | Steve Miller (would be "Miller" if gn is empty) |
| §memberUid|, § | user1, user2 |
Presentation:
The LDAP value will be shown as text.

File upload:
This is used for binary data. You can restrict uploaded data to a given file extension and set the maximum file size.

Presentation:
The uploaded data may also be downloaded via LAM.

The validation expressions follow the standard of Perl regular expressions. They start and end with a "/". The beginning of a line is specified by "^" and the end by "$".
Examples:
/^[a-z0-9]+$/ allows small letters and numbers. The value must not be empty ("+").
/^[a-z0-9]+$/i allows small and capital letters ("i" at the end means ignore case) and numbers. The value must not be empty ("+").
Special characters that must be escaped with "\": "\", ".", "(", ")"
E.g. /^[a-z0-9\.]$/i
This allows your users to setup OpenLDAP TOTP tokens.
Please note that this requires to use a bind user that is also used for all operations. This user needs to be able to add/remove the TOTP object classes and attributes.

On page layout tab you can then add the fields for serial number (optional) and the token. Users will then be able to manage their token via self service.

On module settings tab please provide the DN of your TOTP settings entry (object class "oathTOTPParams").
