LAM currently supports these providers:
privacyIDEA
Base URL: please enter the URL of your privacyIDEA instance
User name attribute: please enter the LDAP attribute name that contains the user ID (e.g. "uid")
Optional: By default LAM will enforce to use a token and reject users that did not setup one. You can set this check to optional. But if a user has setup a token then this will always be required.
Disable certificate check: This should be used on development instances only. It skips the certificate check when connecting to verification server.
Please note that LAM needs to authenticate to privacyIdea with the user's user name and password WITHOUT second factor. This is needed to get the list of tokens that are setup for the user. You can setup a separate policy (scope: authentication) for LAM inside privacyIdea that has IP restriction ("Client" setting) to LAM's server IP and an action "otppin" "none".
YubiKey
Base URLs: please enter the URL(s) of your YubiKey verification server(s). If you run a custom verification API such as yubiserver then enter its URL (e.g. http://www.example.com:8000/wsapi/2.0/verify). The URL needs to end with "/wsapi/2.0/verify". For YubiKey cloud these are "https://api.yubico.com/wsapi/2.0/verify", "https://api2.yubico.com/wsapi/2.0/verify", "https://api3.yubico.com/wsapi/2.0/verify", "https://api4.yubico.com/wsapi/2.0/verify" and "https://api5.yubico.com/wsapi/2.0/verify". Enter one URL per line.
Client id: this is only required for YubiKey cloud. You can register here: https://upgrade.yubico.com/getapikey/
Secret key: this is only required for YubiKey cloud. You can register here: https://upgrade.yubico.com/getapikey/
Optional: By default LAM will enforce to use a token and reject users that did not setup one. You can set this check to optional. But if a user has setup a token then this will always be required.
Disable certificate check: This should be used on development instances only. It skips the certificate check when connecting to verification server.
Duo
This requires to register a new "Web SDK" application in your Duo admin panel.
User name attribute: please enter the LDAP attribute name that contains the user ID (e.g. "uid").
Base URL: please enter the API-URL of your Duo instance (e.g. api-12345.duosecurity.com).
Client id: please enter your client id.
Secret key: please enter your client secret.
WebAuthn/FIDO2
See the WebAuthn/FIDO2 appendix for an overview about WebAuthn/FIDO2 in LAM.
Users will be asked to register a device during login if no device is setup.
Domain: Please enter the WebAuthn domain. This is the public domain of the web server (e.g. "example.com"). Do not include protocol or port. Browsers will reject authentication if the domain does not match the web server domain.
Optional: By default LAM will enforce to use a 2FA device and reject users that do not setup one. You can set this check to optional. But if a user has setup a device then this will always be required.
Okta
This requires to register a new application of type "Web".
There, you will need to configure LAM's 2-factor URLs as "Login redirect URIs" in the new application. They are "https://YOURDOMAIN/lam/templates/login2Factor.php" for admin interface and "https://YOURDOMAIN/lam/templates/selfService/selfService2Factor.php?scope=user&name=YOUR_PROFILE" for self service. You will get an error message during login with the URL to configure in case it was wrong.
On "Sign On" tab you need to add a rule that prompts for the factor.
LAM options:
User name attribute: please enter the LDAP attribute name that contains the user ID (e.g. "mail").
Base URL: please enter the URL of your Okta domain (e.g. https://mydomain.okta.com)
Client id: please enter your application client id.
Secret key: please enter your application secret key.

OpenID
This will use an OpenID server as 2nd factor for authentication.
LAM options:
User name attribute: please enter the LDAP attribute name that contains the user ID (e.g. "uid").
Base URL: please enter the URL of your OpenID client URL. The URL is the one before the "/.well-known/openid-configuration".
Client id: please enter your application client id.
Secret key: please enter your application secret key.
KeyCloack example configuration:
Create a new client, select "OpenID Connect" client type and enter a client ID.

Now enable "Client authentication" and enter the valid redirect URLs in the last step.

They are "https://YOURDOMAIN/lam/templates/login2Factor.php" for admin interface and "https://YOURDOMAIN/lam/templates/selfService/selfService2Factor.php" for self service. You will get an error message during login in case it was wrong. Then save the configuration.
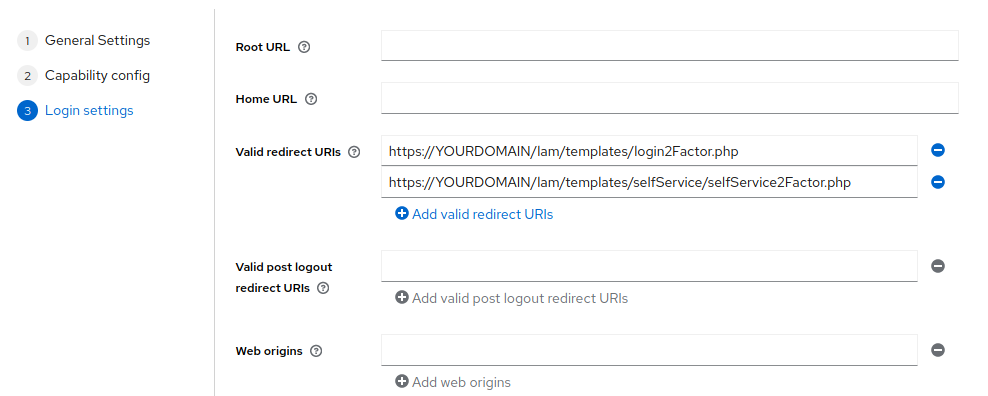
Next, switch to tab "Credentials" to get the client secret.
Example configuration values:
User name: uid
Base URL: http://openidserver/auth/realms/master
Client id: demo
Secret key: 59bdf504-b76e-4138-8421-ef662b2c6c83